A security researcher was recently able to change the top results in Microsoft’s Bing search engine and access any user’s private files, potentially putting millions of users at risk — and all it took was logging into an unsecured web page.
The exploit was discovered by researcher Hillai Ben-Sasson at their team at Wiz, a cloud security firm. According to Ben-Sasson, it would not only allow an attacker to change Bing search results but would also grant them access to millions of users’ private files and data.
Dubbed BingBang by the research group, the vulnerability centered on Microsoft’s Azure Active Directory, which is used by enterprises to manage user identities and access to apps. Unfortunately, if an app is misconfigured, any Azure user in the world can log into it without the proper credentials.
Shockingly, the researchers noted in a technical analysis of the bug that up to 25% of all multi-user apps they scanned were vulnerable — including a Microsoft app named Bing Trivia.
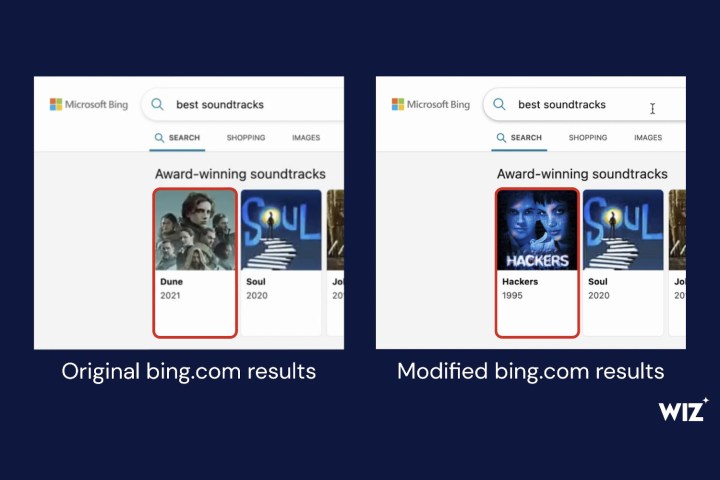
After exploiting the flaw to log into the Bing Trivia app, the Wiz team found a content management system (CMS) tied to Bing.com that was controlling the search engine’s live results. With a touch of humor, they then altered one of the entries, changing the top result for ‘best soundtracks’ from the Dune score to that from the 1995 movie Hackers.
However, there’s nothing funny about what this flaw implies. As the researchers explained, “a malicious actor landing on the Bing Trivia app page could therefore have tampered with any search term and launched misinformation campaigns, as well as phished and impersonated other websites.”
Stealing private files and emails
What’s more, the researchers were able to add a harmless cross-site scripting (XSS) payload into Bing while they were logged in. This was able to run as expected, without interference. After reporting the issue to Microsoft, the researchers tried modifying this XSS payload to see what was possible.
Because Bing integrates with Microsoft 365, the Wiz team was able to create a script that could potentially steal a logged-in user’s access tokens, granting them access to that user’s cloud data. That could include Outlook emails, calendars, Teams messages, OneDrive files, and more.
Put together, that means a hacker could have the power to redirect Bing search results to a malicious website, and at the same time harvest private data from any user logged in on a Microsoft 365 account. All from exploiting a simple login vulnerability.
Fortunately, the researchers immediately reported the flaw to Microsoft and it was patched shortly afterward, resulting in a $40,000 bug bounty reward. Yet it remains an alarming example of how little effort can be required to steal private data from millions of unsuspecting users.


