The best password managers are meant to keep all your logins and credit card info safe and secure, but a major new vulnerability has just put users of the KeePass password manager at serious risk of being breached.
In fact, the exploit allows an attacker to steal a KeePass user’s master password in plain text — in other words, in an unencrypted form — simply by extracting it from the target computer’s memory. It’s a remarkably simple hack, yet one that could have worrying implications.
Password managers like KeePass lock up all your login info to keep it safe, and all that data is sealed behind a master password. You enter your master password to access everything stored in your vault, which makes it a valuable target for hackers.
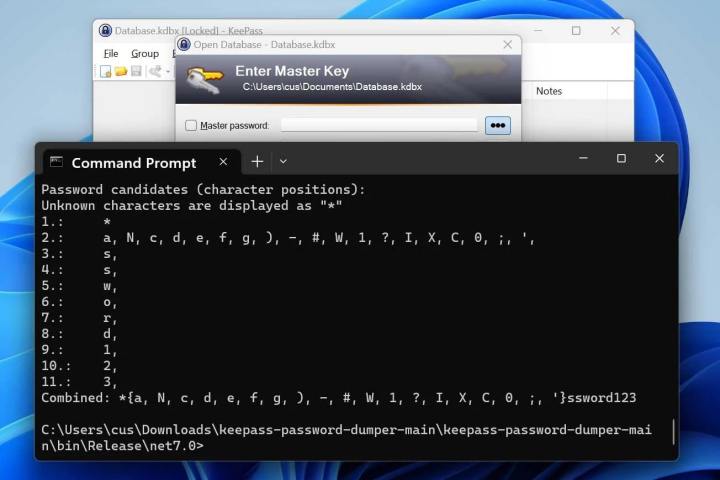
As reported by Bleeping Computer, the KeePass vulnerability was discovered by security researcher ‘vdohney,’ who published a proof-of-concept (PoC) tool on GitHub. This tool is able to extract almost the entire master password (except the first one or two characters) in readable, unencrypted form. It can even do this if KeePass is locked and, potentially, if the app is closed altogether.
That’s because it extracts the master password from KeePass’s memory. As the researcher explains, this can be obtained in a variety of ways: “It doesn’t matter where the memory comes from — can be the process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys) or RAM dump of the entire system.”
The exploit exists thanks to some custom code KeePass uses. When you enter your master password, you do so in a custom box called SecureTextBoxEx. Despite the name, it turns out this box is not so secure after all, since every character typed into the box essentially leaves a leftover copy of itself in the system memory. It’s these remnant characters that the PoC tool finds and extracts.
A fix is coming

The one caveat to this security breach is it requires physical access to the machine from which the master password is to be extracted. But that’s not necessarily always a problem — as we’ve seen in the LastPass exploit saga, hackers can gain access to a target’s computer using vulnerable remote access apps installed on the computer.
If a target computer was infected with malware, it could be configured to dump KeePass’s memory and send both it and the app’s database back to the hacker’s own server, allowing the threat actor to extract the master password in their own time.
Fortunately, KeePass’s developer says a fix is incoming, with one of the possible remedies being to insert random dummy text into the app’s memory that would obfuscate the password. The fix is not expected to be released until June or July 2023, which could be a painful wait for anyone nervous about their master password being leaked. However, the developer has also released a beta version of the fix, which can be downloaded from the KeePass website.
The vulnerability just goes to show that even seemingly secure apps like password managers can be breached, and it’s not the first time a serious weakness has been found in KeePass. If you want to keep yourself safe from online threats like this latest exploit, avoid downloading apps or opening files from unknown senders, steer clear of questionable websites, and use an antivirus app. And, of course, never share your password manager’s master password with anyone.



