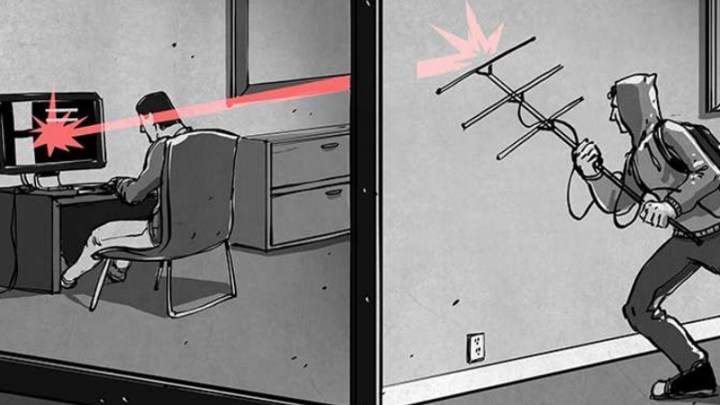
Manufacturing and digital security often have the project management triangle in common. Defeating security and breaching encryption can rarely be done fast, well and without significant cost. But what this Fox-IT technique achieves is very close to that ideal, offering the ability to crack even complex AES-256bit encryption in a few minutes with relatively cheap, off-the-shelf hardware.
Although using more-expensive radio recording hardware can yield better results, the technique is capable of cracking software encryption using just a $25 USB stick and a small wire loop antenna.
By measuring the power output of the encrypting system, the snoopers can tell when an algorithm is receiving input data and later outputting it in an encrypted form. With a mixture of guesswork and correlation, the researchers are able to take that and begin to decode the AES algorithm. By attempting to figure out what the correct value (of 256 options) for each of the 32 bytes is, only 8,192 guesses must be made.
If you were to attempt to brute force hack the encrypted message itself, you’d be making an impossible number of guesses (two, to the power of 256). This technique makes the impossible not only viable but easy.
Better yet, the technique doesn’t require direct access to the encrypting hardware. The researchers were able to perform the technique from up to a meter away.
That was technically only possible because of ideal testing conditions though. In reality, the most even those with high-end equipment could expect to conduct such an attack is from 30 centimeters away. Still, being able to make such an attack from a distance with cheap hardware highlights the potential for new attack vectors against typically near-foolproof encryption systems.
Although breaking open someone’s obfuscated files is almost always going to be easier if you “extract” the decryption key from the owner, this system offers a new way for all sorts of organizations and individuals to target it. In turn, this should lead to better shielding for protected hardware in the future.



