It’s easy to get fooled by this new and devious, holiday-themed phishing attack that offers free prizes. But the old caution that “if it sounds too good to be true, it probably is” continues to be proven correct in this case.
What makes this trick so effective is the elaborate methods used to conceal its nefarious purpose and to reassure you, the potential victim, that it’s perfectly OK to proceed. This phishing attack has actually been active since September and is ongoing, targeting holiday shoppers seeking special offers.

The attack was identified by Akamai and was recently reported on Scam Watcher, where screenshots were also shared, as noted by Bleeping Computer. The carrot that’s dangled is a free gift that is nice, but not so expensive as to be unbelievable. For example, a Yeti Hopper M20 Backpack Cooler was supposedly offered as an incentive to complete a survey.
For those wary of such gifts, scrolling down a bit reveals fake testimonials from people who have supposedly finished the survey and received their reward with no trouble whatsoever. If you were tempted by the gift, this might give you enough reassurance to proceed. There’s one more chance to back out, however.
To receive the free gift, you have to supply your mailing address, which is valuable to scammers. Then there’s the issue of shipping. Since the gift is free, you might not mind paying for shipping. All of this information is easy to enter with your iPhone or Android phone using autofill and it takes seconds to complete the process, nothing compared to the time you’ve already sunk into checking out the freebie, reading testimonials, and taking the survey.
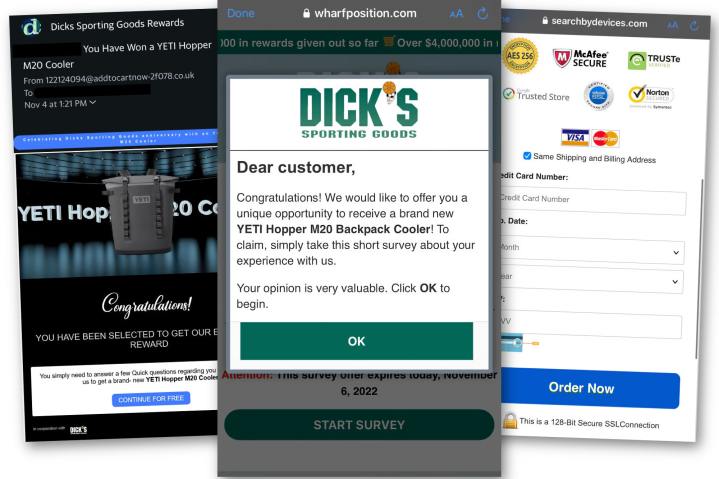
The technical details of this phishing scam are complex and the attack redirects through multiple websites and uses unique website addresses each time, making it difficult to trace back to the perpetrator and shut it down. The best thing for you to do is to use caution and to be very skeptical of these free offers. It’s probably not worth the risk of identity theft, not to mention the financial cost.



