The IRS-authorized tax preparation software service eFile.com recently suffered a JavaScript malware attack in the middle of tax season, according to BleepingComputer.
The nefarious JavaScript file has been identified as popper.js and has been observed by eFile.com users as well as by security researchers. The malware is believed to have surfaced on the service around mid-March and has interacted with “almost every page of eFile.com, at least up until April 1st,” the publication added.
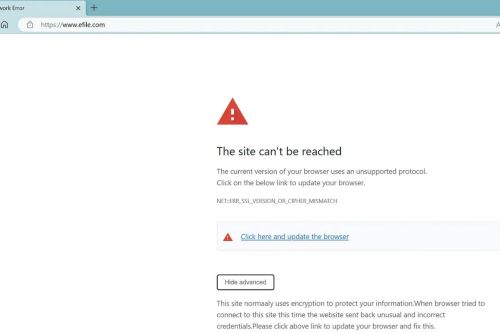
Encountering this infected JavaScript on eFile.com would likely result in seeing a broken link, which is returned by infoamanewonliag[.]online. Users of the service began discussing the possibility of an attack on Reddit on March 17, noting that an SSL error message they were receiving appeared to be fake.
Researchers confirmed that the errors were indicative of a malware attack, also connecting them to the JavaScript malware file update.js. This file acted in the malware as the cue to make users download the file, and can ultimately vary depending on the browser being used, such as [update.exe – VirusTotal] for Chrome or [installer.exe – VirusTotal] for Firefox.
Having conducted its own research on the malware, BleepingComputer learned that the bad actors orchestrating the malware did so from a Tokyo-based IP address, 47.245.6.91 that was likely hosted with Alibaba. The publication also connected the IP address to the infoamanewonliag[.]online domain, which is also associated with the attacks.
BleepingComputer was able to study a sample of the malware script that was uncovered by the Security research group, MalwareHunterTeam, which was written in PHP. The publication determined that the script is a “backdoor malware” that lets hackers control infected devices remotely. Once infected, the PHP script runs in the background, allowing the malware to connect to a device from a control server every ten seconds to perform whatever nefarious actions the bad actor wants.
Despite the malware being a “basic backdoor,” there is a lot of potential for bad actors to use it for very bad purposes including stealing credentials, or stealing data for extortion, the publication noted.
MalwareHunterTeam criticized eFile.com for not addressing the attack for several weeks. It has since been resolved; however, the extent of its impact remains unknown.


