An extensive study reveals that up to 3% of websites may collect your form inputs even before you ever press “Submit.” That’s right — even if you type something and then delete it, these websites will still record your keystrokes and remember the things you chose not to input.
The data, collected without your knowledge and consent, can contain some of the most personal information, that can later be used for various purposes, such as targeted ads.
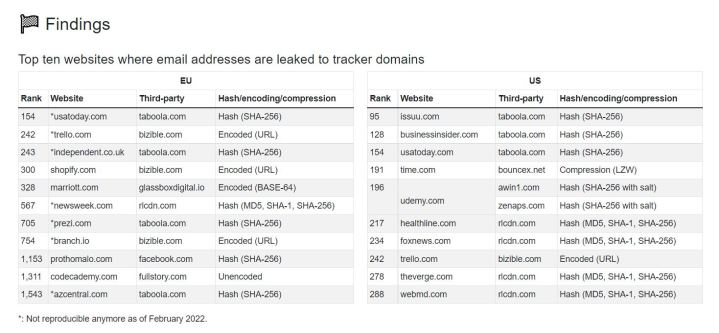
The study is titled, “Leaky Forms: A Study of Email and Password Exfiltration Before Form Submission,” and it was conducted by university researchers on a large sample of 100,000 of the world’s highest-ranking websites, adding up to a total of 2.8 million pages.
Using a website crawler (based on DuckDuckGo’s Tracker Radar Collector) the researchers scoured the internet and came back with staggering results. Although most of us assume that websites only record the things we type when we submit them, it seems that for up to 2,950 sites out of the 100,000 that were sampled, that was simply not true. It seems that, up to 3% of the time, trackers collect data from the moment it’s typed into the form.
Websites use trackers for many reasons, but for the most part, they’re used to personalize your browsing experience as well as collect information about visitor activity. In theory, this is supposed to be anonymous, but of course, personal identifiers narrow things down a whole lot.
Trackers can be useful, as they let the websites know what kind of content the users are most interested in. However, third-party trackers are used to help advertisers ensure that the ads you see are targeted, meaning you’d be more likely to click and purchase something.
The crawler used in the research was equipped with a machine learning classifier that was previously trained to detect email and password fields, and then intercept any potential script access to those fields. It seems that many third-party trackers have been caught using scripts that monitor the keystrokes when the visitor types inside a form. If the trackers save the information before it is submitted, some of them would be able to collect email addresses and passwords without the user’s consent.
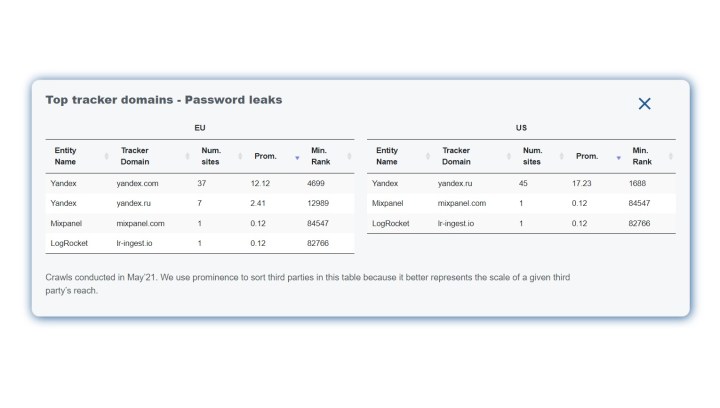
The fact that some third-party trackers were able to collect keystrokes, and thus data, prior to anything being submitted, is definitely alarming. According to the researchers, this issue affects a small percentage of trackers, but they are quite prevalent on the web. The biggest culprits were LiveRamp (662 websites), Taboola (383), Verizon (255), and Bizible (191). These trackers were present on websites where email addresses were logged. When it comes to snatching passwords, Yandex trackers top the list.
An interesting factor of the research is that European users were subjected to fewer attempts of email/password extraction than the users in the U.S. Only 1,844 websites allowed trackers to do this when visited from Europe, compared to 2,950 for users in the United States.
Users in Europe are protected by the GDPR, a set of legal regulations concerning personal data. According to the study, email exfiltration via trackers breaches at least three GDPR laws. Violating the GDPR can result in enormous fines reaching as high as 20 million euros or up to 4% of the global annual turnover of the entity in question.
The highlights from the study were published by researchers alongside a full, much more technical version for those who want to learn a bit more. This was then first shared by Bleeping Computer. It’s important to note that half of the listed first and third parties responded to the researchers and claimed that the collection was due to a mistake.
If you want to protect yourself from similar trackers, it might be a good idea to disable third-party trackers altogether — you can do this in your browser settings. It’s also considered good practice to change your password every so often. Password managers can prove helpful if you’re juggling a lot of different passwords that change on a regular basis.



