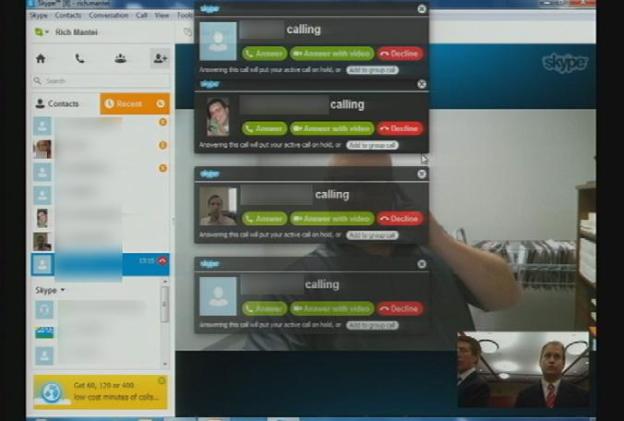
Detailed by CBS News yesterday, the George Zimmerman murder trial was disrupted on Wednesday when several Internet pranksters tried to Skype call Rich Mantei, the prosecutor of the case. At the time, a former criminal justice professor that taught Zimmerman, Gordon Scott Pleasants, was giving video testimony over Skype. It was extremely easy to get both Skype usernames since national news networks were broadcasting live coverage of the trial and the attorneys left both Skype names visible on the television screen rather than using full screen video mode to hide all contact information.

All the notifications on the courtroom’s end were popping up all over the television screen, thus hiding the face of Pleasants while he was attempting to provide testimony. The attorneys scrambled to close the Skype notifications while the exasperated judge requested another form of communication for the testimony.
If the attorneys had taken a couple minutes to familiarize themselves with the Skype settings prior to the start of the testimony, they would have found an option to limit calls from people in their Contact list only in addition to options for turning off all notifications as well as muting all sounds played by the notifications. In fact, they didn’t even need the audio on the computer turned on since Pleasants was communicating over a regular phone.
Regarding alternatives to Skype, going with a Google+ hangout for the video feed could have avoided this issue. It’s definitely clear that the Zimmerman case will be used as an example of what not to do in the future when video chatting tools like Skype are combined with a national audience of television viewers.


