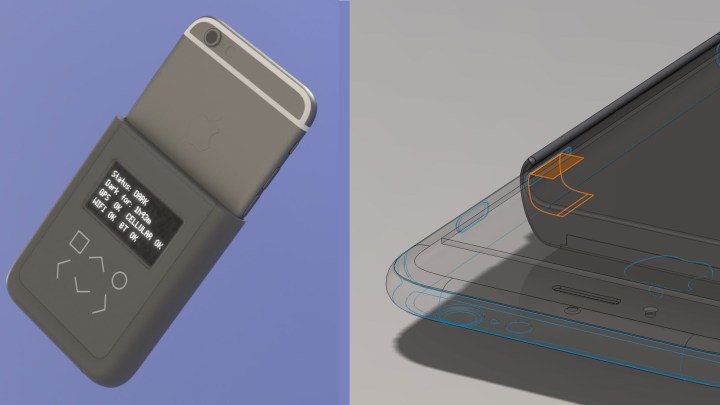
Snowden and Huang presented details on their tool during the recent Forbidden Research talk (video) at MIT’s Media Lab and published a technical paper that describes the scope of the problem and their proposed solution. The core of their tool is an open-source and user-inspectable introspection engine that monitors radio transmissions and alerts the owner when their phone is transmitting its location even though it is supposed to be in airplane mode. Users can check their phone in the field and confirm in real-time that it’s secure. All this monitoring hardware will be embedded in a battery case that looks innocuous from the outside.
The proposed hardware resides outside the scope of the phone’s CPU and other internal hardware, allowing it to operate autonomously without being compromised by the monitoring and tracking systems embedded into the phone. It is covert enough to perform its monitoring without being detected by the operating system of the phone and has safeguards to prevent false negative or positive alerts. Snowden and Huang want their proposed security system to be accessible to a variety of users and have designed it with an intuitive interface that requires only minimal input from the user.
To streamline development of the hardware, Snowden and Huang chose the iPhone 6 as the first phone for field development of their tool. This model was chosen, not because it was more susceptible to attack, but because it is one of the most popular smartphones among journalists.
“The choice of model is driven primarily by what we understand to be the current preferences and tastes of reporters,” the pair noted in their report. “It has little to do with the relative security of any platform, as we assume any platform, be it iOS or Android, can and will be compromised by state-level adversaries.” Snowden and Huang obtained detailed iPhone schematics and components from China’s electronics markets and used this information to reverse-engineer the phone’s hardware and aid in the design of their introspection engine.
Though they chose to focus on the iPhone and its radio hardware, Snowden and Huang expect this technology to expand to other core hardware systems and even other smartphones in the future. They note that systems such as the filesystem can be monitored using an introspection engine attached to a mass storage device. The pair also point out in their paper that minimal phone hardware design changes, such as grouping radio control test points together, could make it easier to develop the introspection engine for future smartphone models.



