The Canon Pixma uses a Web interface so that owners can check on its status remotely. Mr. Jordon found that the interface does not require a username or password, so anyone could check on the device’s status once they found it. This did not seem like a problem until he realized that it is also possible to update the device’s firmware through the remote Web interface. Although the firmware is encrypted, Mr. Jordon was able to crack it and thus convince the printer to accept his own, re-written firmware.
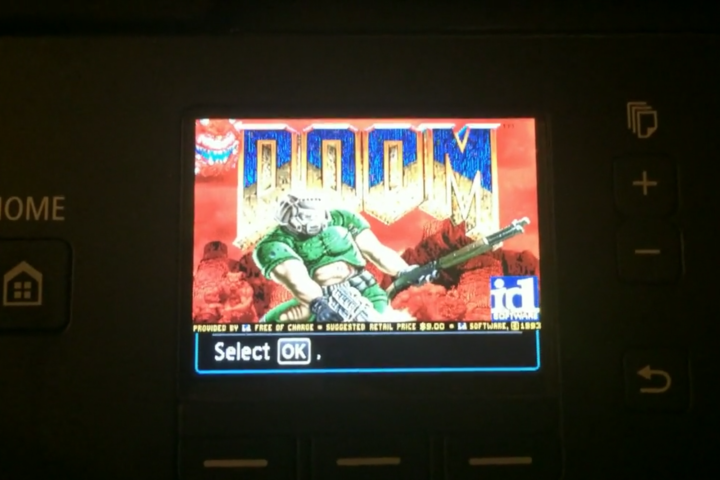
That’s when he got the idea to run Doom, which has become a de facto “Hello, World!” program for hackers to demonstrate mastery over a given device. Doom has been implemented on everything from ATMs to graphic calculators. “Running Doom, that’s real proof you control the thing,” Jordon told the BBC.
Related: The return of Doom will be teased in an upcoming beta
Although the printer’s 32-bit ARM processor and 10MB of memory was more than sufficient in terms of raw power, the lack of a conventional operating system meant that it took months of coding and experimentation so the game could deal with the printer’s idiosyncrasies. The color palette is off, but the game works sufficiently to prove Mr. Jordon’s point, and he has no plans to further optimize it.
In response to Mr. Jordon’s work, Canon has promised “to provide a fix as quickly as is feasible,” adding a username and password to all future Pixma printers and providing an update for all models launched from the second half of 2013 onward. A quick search on the Shodan search engine reveals that there are thousands of unsecured printers out there on the Web, though Mr. Jordon has found no evidence of anyone abusing the loophole.
For a more technically in-depth explanation of how Jordon hacked the printers’s encryption, check out his blog post over at the site of his employer, Context Information Security.


